9. General Settings » Custom Decoders¶
Decoders are internal functions (traffic dissectors) that identify and categorize the protocols in each packet or flow. Dozens of built-in decoders come pre-installed. If you don’t require custom decoders, you can safely skip this section.
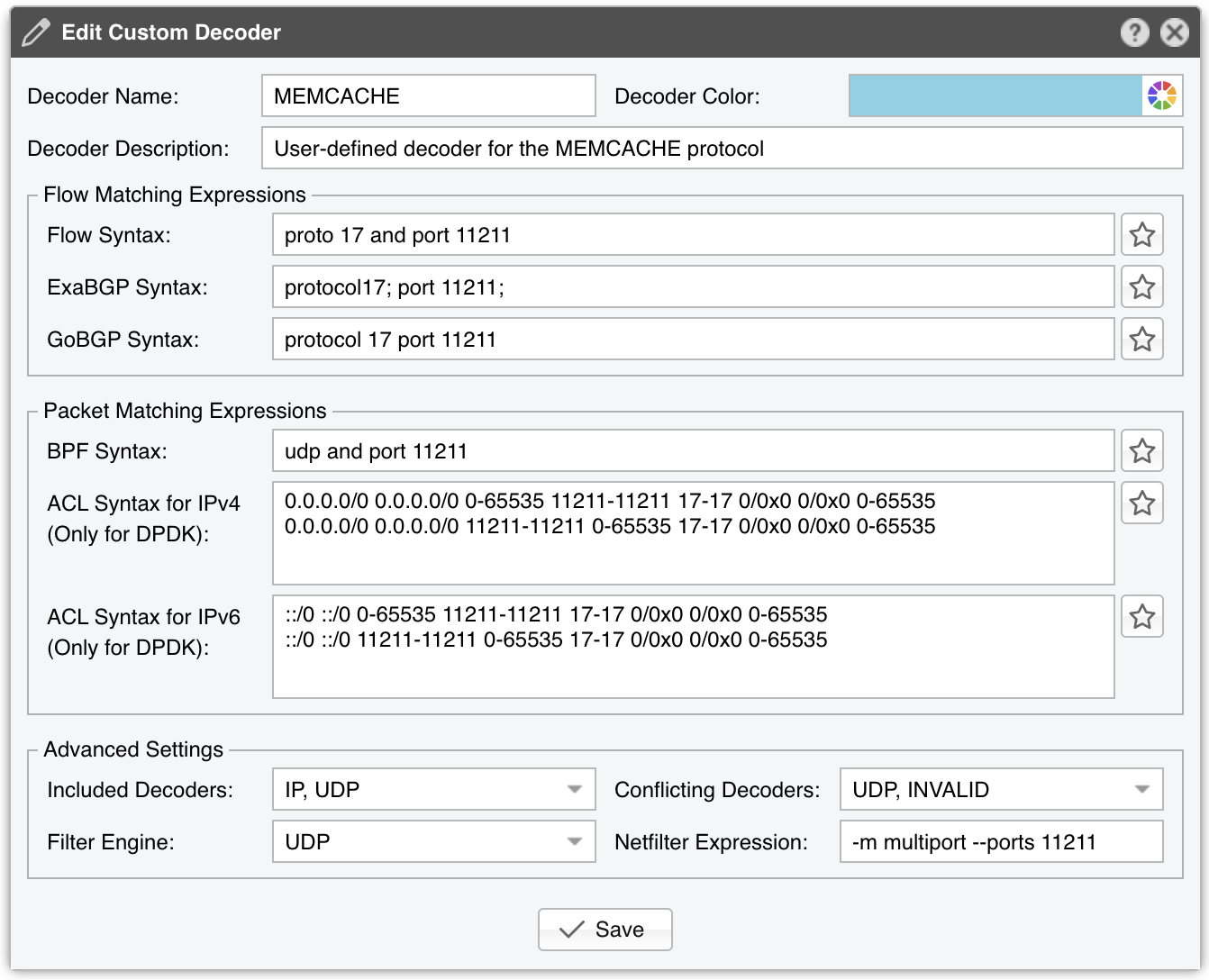
To manage user-defined decoders, go to Configuration » General Settings » Custom Decoders. Each custom decoder is defined by the following parameters:
Note
To generate IP Graphs, Tops and Accounting data for a custom decoder, enable it in Configuration » General Settings » Graphs & Storage. To use the decoder for thresholds, enable it in Configuration » General Settings » Anomaly Detection.
9.1. Built-in Decoders¶
IP |
Matches all IP packets, regardless of higher-layer protocols. Always enabled. |
TCP |
Matches TCP traffic |
TCP+SYN |
Matches TCP traffic with the SYN flag set and ACK unset. Flow Sensor counts one packet per flow |
UDP |
Matches UDP traffic |
ICMP |
Matches ICMP traffic |
OTHER |
Matches IP protocols other than TCP, UDP, and ICMP |
INVALID |
Matches TCP or UDP port 0, or IP protocol 0 |
FLOWS |
Matches flow records and replaces packets/s with flows/s. Works only with Flow Sensor |
FLOW+SYN |
Matches flow records with the SYN flag set. Flow Sensor counts all packets per flow |
FRAGMENT |
Matches fragmented IP packets. Works only with Packet Sensor |
TCP-NULL |
Matches TCP traffic without TCP flags (indicative of reconnaissance sweeps) |
TCP+RST |
Matches TCP traffic with the RST flag set |
TCP+ACK |
Matches TCP traffic with the SYN flag unset and ACK set |
TCP+SYNACK |
Matches TCP traffic with both SYN and ACK flag set |
NETBIOS |
Matches TCP traffic on source or destination port 139 |
QUIC |
Matches Google’s QUIC protocol on UDP ports 80 and 443 |
UDP-QUIC |
Matches UDP traffic that is not part of the QUIC protocol |
MEMCACHED |
Matches UDP traffic on port 11211 |
HTTP |
Matches TCP traffic on source or destination port 80 |
HTTPS |
Matches TCP traffic on source or destination port 443 |
Matches TCP traffic on source or destination ports 25, 110, 143, 465, 585, 587, 993, 995 |
|
DNS |
Matches UDP traffic on source or destination port 53 |
SIP |
Matches TCP or UDP traffic on source or destination port 5060 |
IPSEC |
Matches IP traffic on IP protocols 50 or 51 |
WWW |
Matches TCP traffic on source or destination ports 80 or 443 |
SSH |
Matches TCP traffic on source or destination port 22 |
NTP |
Matches UDP traffic on source or destination port 123 |
SNMP |
Matches UDP traffic on source or destination ports 161 or 163 |
RDP |
Matches TCP or UDP traffic on source or destination port 3389 |
YOUTUBE |
Matches IP traffic to or from YouTube AS 43515, 36561, or YouTube subnets |
NETFLIX |
Matches IP traffic to or from Netflix AS 55095, 40027, 2906, or Netflix subnets |
HULU |
Matches IP traffic to or from Hulu AS 23286 or Hulu subnets |
Matches IP traffic to or from Facebook AS 54115, 32934, or Facebook subnets |