24. Network & Policy » Whitelist Template¶
Whitelists can be used to prevent Wanguard Filter from blocking traffic you consider essential. By default, during inbound attacks, destination ports and IPs are blocked only in worst-case scenarios when no other attack pattern is identified. However, sometimes it’s preferable to allow possibly malicious traffic to enter rather than risk blocking critical traffic.
You can assign whitelist rules directly to each Filter defined in Configuration » Components. But if you need the same whitelist rules across multiple Filters, it’s simpler to put them in a Whitelist Template and apply that template to the Filters that require it.
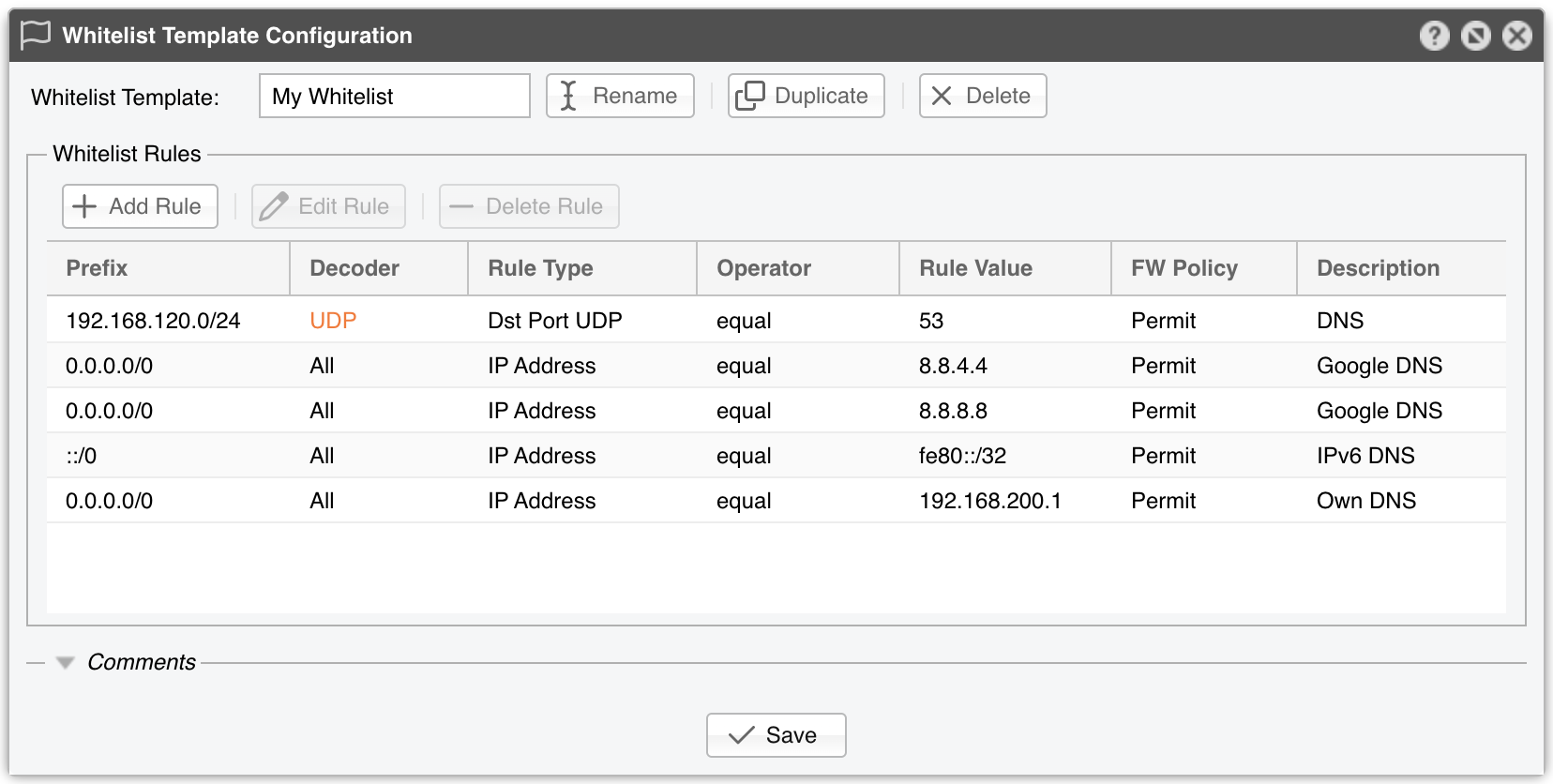
Each whitelist rule defines several metrics:
● Prefix – The whitelist rule is evaluated only if the anomaly’s IP address is included in this prefix. 0.0.0.0/0 matches any IPv4, ::/0 matches any IPv6, /0 matches any IP
● Decoder – The decoder this whitelist rule applies to, or All to match any decoder used by the anomaly
● Rule Type – Possible options: IP Address, Src Port TCP, Dst Port TCP, Src Port UDP, Dst Port UDP, ICMP Type, Packet Length, IP TimeToLive, IP Protocol
● Operator – Operators for strings/numbers include equal and non-equal. Numbers also support less than and greater than. equal can match IP addresses in CIDR notation, port ranges (e.g., <port_min>:<port_max>), or packet size ranges (<pkt_size_min>:<pkt_size_max>)
● Rule Value – The custom value defined by the user
● FW Policy – If set to Permit and Operator is equal, the Filter explicitly allows the matched traffic through the Netfilter firewall. Otherwise, broader filtering rules may override it
● Comments – (Optional) A short description of the whitelist rule
For example, if your DNS server on port 53/UDP is attacked by spoofed addresses, the software may block traffic to that server on 53/UDP, making it partially unreachable from the Internet. Avoid this scenario by adding the whitelist rule [Prefix = your DNS server, Decoder = ANY, Rule Type = Dst Port UDP, Operator = equal, Rule Value = 53, FW Policy = Permit].
You can set the priority of the filtering rules in General Settings » Anomaly Mitigation.
Note
When a filtering rule matches a whitelist entry, it appears with a white flag. However, it is never applied to the firewall.