17. Components » Flow Sensor¶
Most routers and many enterprise switches can collect IP traffic statistics and export them as flow records to Flow Sensor. Because the flow protocol pre-aggregates traffic data, the flows sent to Flow Sensor are significantly smaller than the traffic being monitored. This makes Flow Sensor ideal for monitoring remote or high-traffic networks. For a comparison of flow-based and packet-based monitoring, see the Choosing a Method of Traffic Monitoring chapter.
Appendix 2 shows how to enable NetFlow, sFlow, or IPFIX on a number of devices, but the best and most up-to-date instructions can only be found in the vendor’s documentation.
To add a Flow Sensor, click [+] in the title bar of the Configuration » Components panel. To modify an existing Flow Sensor, go to Configuration » Components and click its name.
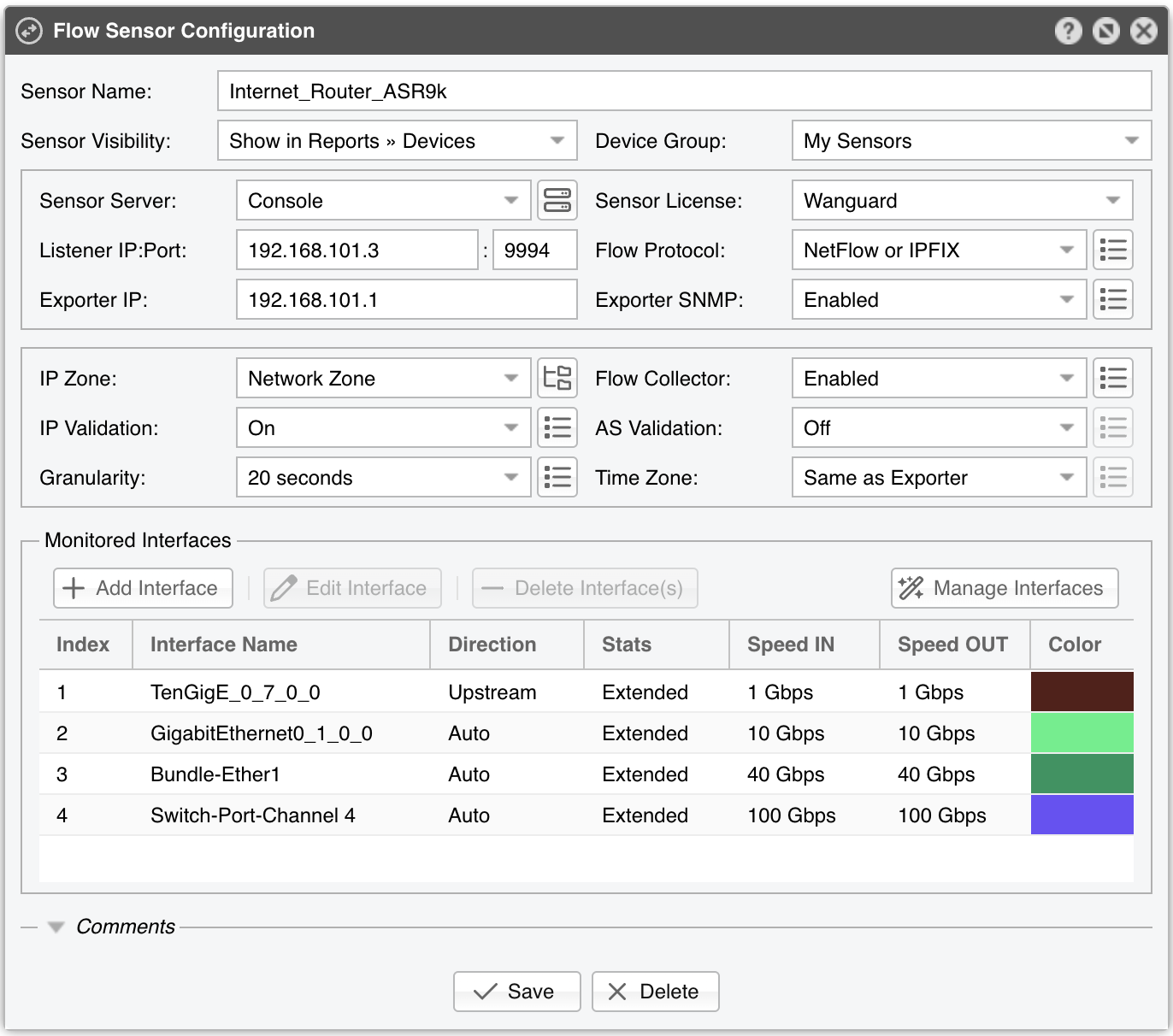
Flow Sensor Configuration parameters:
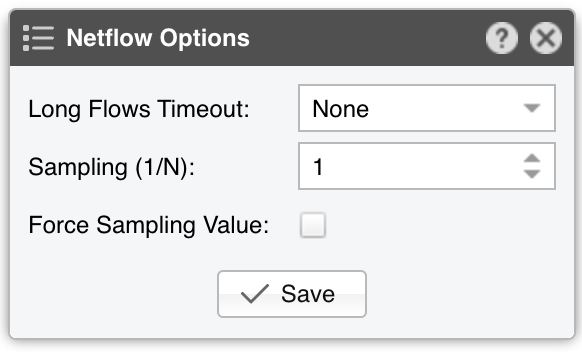
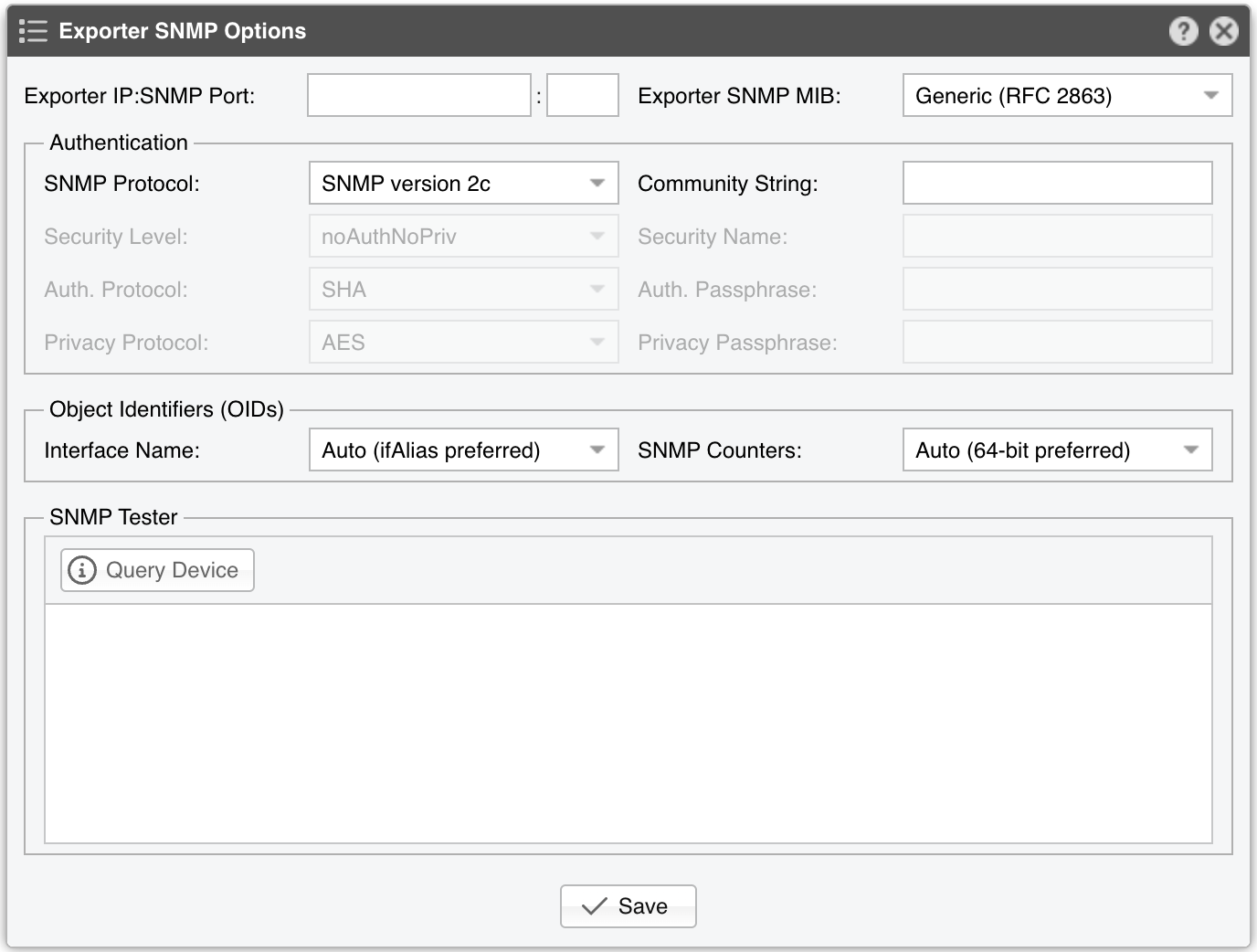
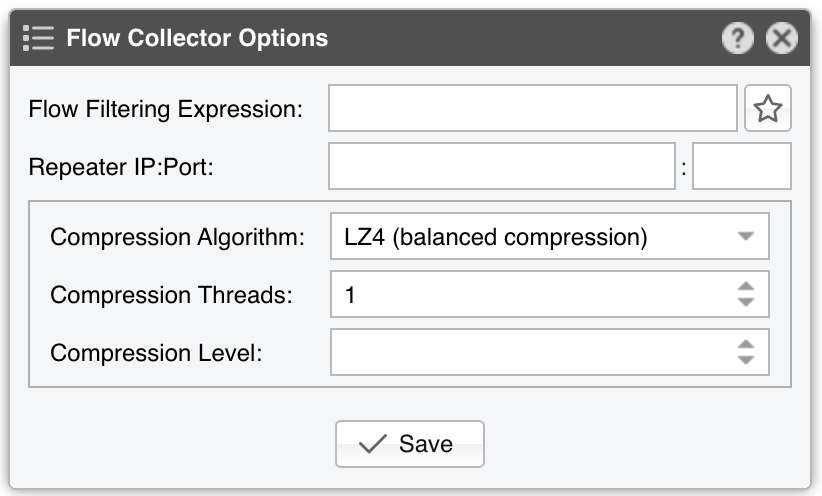
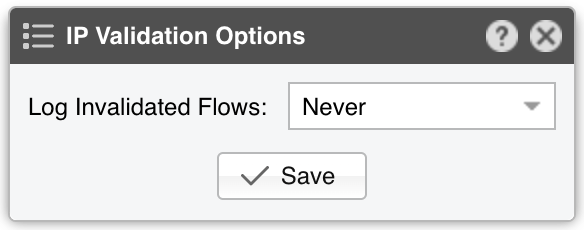
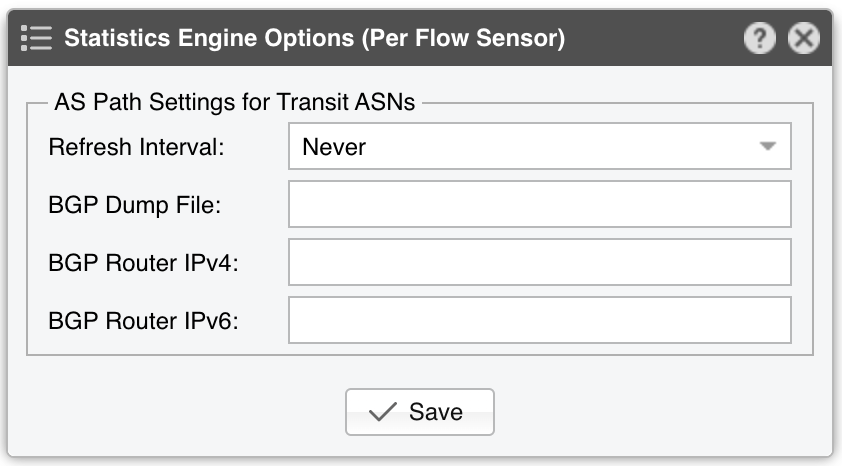
● Sensor Name – A short name to identify the Flow Sensor● Sensor Visibility – Controls whether the Flow Sensor appears in Reports » Devicesa● Device Group – Optional label for organizing components by location, characteristics, or for granular role-base access● Sensor Server – Select a server that fulfills the minimum system requirements for running the Flow Sensor. If this is not the Console server, follow the NFS configuration steps to make the flow data visible in the web interface● Sensor License – The license used by the Flow Sensor. Wanguard provides all features; Wansight does not provide traffic anomaly detection and reaction● Listener IP:Port – The IP address (IPv4 or IPv6) and destination port on which flow packets are received. Each flow exporter must use a unique destination port if multiple exporters are sending flows to the same server● Flow Protocol – The flow protocol used by the flow exporter:▪ Netflow or IPFIX – Select if your router exports NetFlow v5, v7, v9 or IPFIX, then click on the options button on the right-hand side of the field for Netflow-specific options:• Long Flows Timeout – For routers like Juniper MX that maintain the start time of previously exported flows, set this to the flow active/inactive timeout in the router’s config (commonly 60 seconds). For other exporters, leave None• Sampling (1/N) – Enter the sampling rate configured on the exporter, or leave the default if no sampling is set• Force Sampling Value – Override the exporter’s reported sampling value if misread▪ sFlow – Choose this if your router exports flows using the sFlow protocol● Exporter IP – IP address of the flow exporter (router, switch, or probe). For sFlow, specify the IP actually sending the flow packets (not the Agent IP)● Exporter SNMP – You must enable SNMP on the flow exporter to allow Console to extract interface information automatically▪ Enabled – Click the Options button beside Exporter SNMP to configure:▪ Disabled – If SNMP is not set up, you must manually add each interface and specify its SNMP index, speed, etc.● IP Zone – Flow Sensor uses the IP Zone to learn the network’s boundaries and apply per-subnet setting● Flow Collector – When enabled, raw flow data is saved to disk. You can query flow records in Reports » Tools » Flows, and limit disk usage in General Settings » Data Retention• Flow Filtering Expression - Restricts which flows are analyzed. Click the bookmark icon to see the correct syntax• Repeater IP:Port – Enter the IP and port of another flow collector to which Flow Sensor will forward flow packets• Compression Algorithm - Flow Sensor supports LZO, BZ2, LZ4, or ZSTD for compressing raw flow data. LZO is fastest, BZ2 has the best compression ratio (though ~30 times slower), and LZ4/ZSTD balance speed and efficiency• Compression Threads - Allows multiple threads for compressing raw flows. Typically, 1 thread suffices. If CPU usage exceeds 50%, consider raising this number• Compression Level - For LZ4 or ZSTD, specify a custom level. If empty or 0, the default compression level is used● IP Validation – This parameter is frequently used for distinguishing the traffic’s direction (relative to the monitored network):▪ Off – Disables IP Validation▪ On – Flow Sensor examines only flows in which the source IP and/or destination IP belongs to the IP Zone. Traffic with a destination IP in the IP Zone is inbound. Traffic with a source IP in the IP Zone is outbound. This simplifies interface configuration (direction can be Auto), but inbound/outbound traffic is considered entering/exiting the network, rather than a specific interface (like SNMP Sensor and any other SNMP-based tool)• Log Invalidated Flows – When set to Periodically, the event log shows the percentage of invalidated flows and lists ten flows that fail IP validation once every ten ticks▪ Strict – Flow Sensor processes only flows where either the source or the destination IP is in the IP Zone▪ Exclusive – Flow Sensor processes only flows with a destination IP inside the IP Zone● AS Validation – BGP-enabled routers can export flows that contain the source and destination ASN (Autonomous System Number). In most cases, if the AS number is set to 0, then the IP address belongs to the local ASN. This option is rarely used for establishing traffic direction. AS Validation provides three choices:▪ Off – Disables AS validation▪ On – Flow Sensor processes only flows in which the source ASN and/or destination ASN is in the Local AS List (defined below).• Local AS List – Enter your AS numbers, separated by spaces• Log Invalidated Flows – When set to Periodically, the event log reports the percentage of invalidated flows and shows ten flows that fail AS validation every ten ticks▪ Strict – Flow Sensor processes only flows in which either the source or destination ASN is in the Local AS List● Granularity – Lower values improve Sensor graph accuracy but consume more RAM. The default 20-second interval is recommended for most setups• Anomaly Granularity – How often to check for new anomalies• Interface Threads – How many threads to use when analyzing interface data. The default is a thread for each 10 interfaces● Time Zone – Indicate the offset between the Flow Sensor server’s time zone and that of the flow exporter. It’s crucial to run NTP on both devices to keep their clocks in sync● Monitored Interfaces – This grid lists all interfaces to be monitored. To avoid duplicate flow entries, it’s best to add only upstream interfaces. Click Add Interface to add interfaces one by one, or click Manage Interfaces to add multiple interfaces in bulk▪ SNMP Index – Each interface is identified by its SNMP index. If SNMP is configured, Flow Sensor can auto-fill this number. Otherwise, retrieve it from the flow exporter and enter it manually▪ Interface Name – Short descriptive name for the monitored interface. Descriptions longer than ten characters may clutter some reports▪ Interface Color – Used in graphs. The default is random, but you can choose a different color from the drop-down menu▪ Traffic Direction – Defines how traffic entering the interface relates to your network:• Auto – Recommended in most scenarios. Direction is determined by IP/AS Validation or by the router (if supported in flow data)• Upstream – For peering or internet-facing interfaces• Downstream – For interfaces connected to your own network or customers• Null – Traffic on these interfaces is discarded and thus ignored by Flow Sensor▪ Stats Engine – Determines which traffic tops and AS (Autonomous System) data are collected:• Basic – Enables tops for internal IPs (IPs within the IP Zone), IP protocols, TCP/UDP ports, and IP versions• Extended – Includes Basic tops plus upstream ASNs and countries. If the router doesn’t export AS info in flows (e.g., non-BGP router), Flow Sensor uses a GeoIP database that might be slightly outdated. Performance impact is minimal◦ Refresh Interval – Specifies how often the MRT file is reloaded in RAM. If set to Auto, it reloads whenever modified. If set to Never, it loads only when the Sensor starts◦ BGP Dump File – If this field points to a valid BGPd MRT file file, Flow Sensor can show tops and graphs for Transit ASNs◦ BGP Router IPv4/IPv6 – If you’ve specified a BGP Dump File, also enter the next-hop router’s IP address(es). You can find the NEXT_HOP in bgpdump output• Full – Includes everything from Extended, plus external IPs (those not in the IP Zone). This setting can significantly increase RAM usage during spoofed attacks with randomized source IPs. It also enables threshold detection for external IPs, and ensures more accurate live AS and country stats▪ Link Speed In & Link Speed Out – Specify the interface’s bandwidth or capacity. These values enable percentage-based reports and bits/s thresholds● Comments – Enter remarks about the Flow Sensor. These notes are for internal reference only and will not appear elsewhere
Note
For more details on attack sources detected by Flow Sensor, add a Flow Filter (default parameters are fine) and enable it in the “When an anomaly is detected…” panel of the Response. If the network supports BGP Flowspec, you can also mitigate DDoS attacks directly on the router by configuring a GoBGP Connector or ExaBGP Connector.
17.1. Flow Sensor Troubleshooting¶
[root@localhost ~]# tcpdump -i <interface_eth0_p1p1_etc> -n -c 100 host <flow_exporter_ip> and udp and port <destination_port>
[root@localhost ~]# ufw status || firewall-cmd --list-all || iptables -L -n -v && iptables -t raw -L -n -v
[root@localhost ~]# ntpq -p || chronyc tracking || timedatectl status
[root@localhost ~]# netstat -s | grep Filter
Received flow <starting/ending> <X> seconds ago, check the following:set forwarding-options sampling instance NETFLOW family inet output inline-jflow flow-export-rate 40
Sensor frozen for <X> seconds. Restarting the collector can have several causes. It is generated when the flow packets are too scarce (1 every few seconds), or when flow packets are not received for tens of seconds (e.g., due to a network outage or router reload). Another cause indicates a performance issue, with the Flow Sensor not having enough CPU and I/O resources to analyze traffic and send data to the SQL server in a timely manner. In this case, use a physical server instead of a virtual machine, or decrease from the IP Zone the IP graphs and IP accounting data that need to be collectedset chassis fpc inline-services flow-table-size ipv4-flow-table-size 15
[root@localhost ~]# tcpdump -i <interface_eth0_p1p1_etc> -s0 -w flows.pcap -c 10000 host <flow_exporter_ip> and udp and port <destination_port>
License key not compatible with the existing server indicates that the server is unregistered and you need to send the string from Configuration » Servers » [Server] » Hardware Key to sales@andrisoft.com